Category: News
New 'Cuckoo' Persistent macOS Spyware Targeting In...
Cybersecurity researchers have discovered a new information stealer targeting Apple macOS systems that's designed to set up persis...
Microsoft Outlook Flaw Exploited by Russia's APT28...
Czechia and Germany on Friday revealed that they were the target of a long-term cyber espionage campaign conducted by the Russia-l...
Expert-Led Webinar - Uncovering Latest DDoS Tactic...
In today's rapidly evolving digital landscape, the threat of Distributed Denial of Service (DDoS) attacks looms more significant t...
Hackers Increasingly Abusing Microsoft Graph API f...
Threat actors have been increasingly weaponizing Microsoft Graph API for malicious purposes with the aim of evading detection. Thi...
New Guide Explains How to Eliminate the Risk of Sh...
SaaS applications are dominating the corporate landscape. Their increased use enables organizations to push the boundaries of tech...
NSA, FBI Alert on N. Korean Hackers Spoofing Email...
The U.S. government on Thursday published a new cybersecurity advisory warning of North Korean threat actors' attempts to send ema...
Google Announces Passkeys Adopted by Over 400 Mill...
Google on Thursday announced that passkeys are being used by over 400 million Google accounts, authenticating users more than 1 bi...
Four Critical Vulnerabilities Expose HPE Aruba Dev...
HPE Aruba Networking (formerly Aruba Networks) has released security updates to address critical flaws impacting ArubaOS that coul...
Popular Android Apps Like Xiaomi, WPS Office Vulne...
Several popular Android applications available in Google Play Store are susceptible to a path traversal-affiliated vulnerability c...
Ukrainian REvil Hacker Sentenced to 13 Years and O...
A Ukrainian national has been sentenced to more than 13 years in prison and ordered to pay $16 million in restitution for carrying...
When is One Vulnerability Scanner Not Enough?
Like antivirus software, vulnerability scans rely on a database of known weaknesses. That’s why websites like VirusTotal exist, to...
Dropbox Discloses Breach of Digital Signature Serv...
Cloud storage services provider Dropbox on Wednesday disclosed that Dropbox Sign (formerly HelloSign) was breached by unidentified...
New "Goldoon" Botnet Targets D-Link Routers With D...
A never-before-seen botnet called Goldoon has been observed targeting D-Link routers with a nearly decade-old critical security fl...
CISA Warns of Active Exploitation of Severe GitLab...
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a critical flaw impacting GitLab to its Known Exploited...
New Cuttlefish Malware Hijacks Router Connections,...
A new malware called Cuttlefish is targeting small office and home office (SOHO) routers with the goal of stealthily monitoring al...
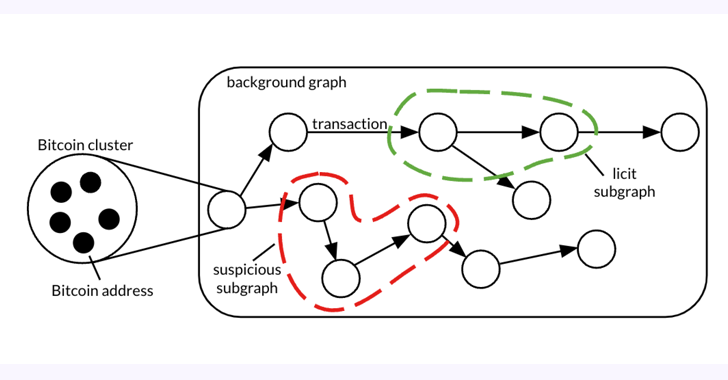
Bitcoin Forensic Analysis Uncovers Money Launderin...
A forensic analysis of a graph dataset containing transactions on the Bitcoin blockchain has revealed clusters associated with ill...
How to Make Your Employees Your First Line of Cybe...
There’s a natural human desire to avoid threatening scenarios. The irony, of course, is if you hope to attain any semblance of sec...
NBA doesn't suspend Nuggets' Jamal Murray, but fin...
Denver Nuggets star guard Jamal Murray avoided a suspension from the NBA, but he was issued a hefty fine for tossing a towel and h...
Mitchell Robinson likely to miss rest of playoffs ...
Knicks center Mitchell Robinson suffered a "stress injury" to his left ankle, an injury he dealt with earlier this season, that wi...
Sharks general manager doesn't shy away from who f...
The San Jose Sharks won the NHL Draft Lottery on Tuesday, and general manager Mike Grier did not shy away from who the team will b...