Category: Hacker News
Critical Tinyproxy Flaw Opens Over 50,000 Hosts to...
More than 50% of the 90,310 hosts have been found exposing a Tinyproxy service on the internet that's vulnerable to a critical unp...
Russian Operator of BTC-e Crypto Exchange Pleads G...
A Russian operator of a now-dismantled BTC-e cryptocurrency exchange has pleaded guilty to money laundering charges from 2011 to 2...
Google Simplifies 2-Factor Authentication Setup (I...
Google on Monday announced that it's simplifying the process of enabling two-factor authentication (2FA) for users with personal a...
New Case Study: The Malicious Comment
How safe is your comments section? Discover how a seemingly innocent 'thank you' comment on a product page concealed a malicious v...
China-Linked Hackers Used ROOTROT Webshell in MITR...
The MITRE Corporation has offered more details into the recently disclosed cyber attack, stating that the first evidence of the in...
APT42 Hackers Pose as Journalists to Harvest Crede...
The Iranian state-backed hacking outfit called APT42 is making use of enhanced social engineering schemes to infiltrate target net...
Russian Hacker Dmitry Khoroshev Unmasked as LockBi...
The U.K. National Crime Agency (NCA) has unmasked the administrator and developer of the LockBit ransomware operation, revealing i...
Ex-NSA Employee Sentenced to 22 Years for Trying t...
A former employee of the U.S. National Security Agency (NSA) has been sentenced to nearly 22 years (262 months) in prison for atte...
ZLoader Malware Evolves with Anti-Analysis Trick f...
The authors behind the resurfaced ZLoader malware have added a feature that was originally present in the Zeus banking trojan that...
Everyone's an Expert: How to Empower Your Employee...
There’s a natural human desire to avoid threatening scenarios. The irony, of course, is if you hope to attain any semblance of sec...
Android Malware Wpeeper Uses Compromised WordPress...
Cybersecurity researchers have discovered a previously undocumented malware targeting Android devices that uses compromised WordPr...
Webinar: Learn Proactive Supply Chain Threat Hunti...
In the high-stakes world of cybersecurity, the battleground has shifted. Supply chain attacks have emerged as a potent threat, exp...
Apache Cordova App Harness Targeted in Dependency ...
Researchers have identified a dependency confusion vulnerability impacting an archived Apache project called Cordova App Harness. ...
CoralRaider Malware Campaign Exploits CDN Cache to...
A new ongoing malware campaign has been observed distributing three different stealers, such as CryptBot, LummaC2, and Rhadamanthy...
eScan Antivirus Update Mechanism Exploited to Spre...
A new malware campaign has been exploiting the updating mechanism of the eScan antivirus software to distribute backdoors and cryp...
Major Security Flaws Expose Keystrokes of Over 1 B...
Security vulnerabilities uncovered in cloud-based pinyin keyboard apps could be exploited to reveal users' keystrokes to nefarious...
Researchers Detail Multistage Attack Hijacking Sys...
Cybersecurity researchers have discovered an ongoing attack campaign that's leveraging phishing emails to deliver a malware called...
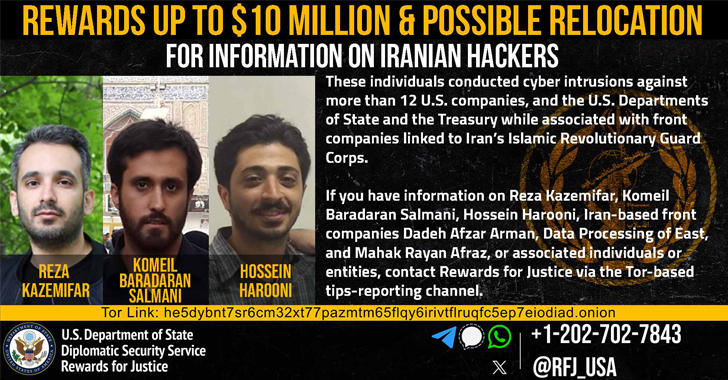
U.S. Treasury Sanctions Iranian Firms and Individu...
The U.S. Treasury Department's Office of Foreign Assets Control (OFAC) on Monday sanctioned two firms and four individuals for the...
State-Sponsored Hackers Exploit Two Cisco Zero-Day...
A new malware campaign leveraged two zero-day flaws in Cisco networking gear to deliver custom malware and facilitate covert data ...
Google Postpones Third-Party Cookie Deprecation Am...
Google has once again pushed its plans to deprecate third-party tracking cookies in its Chrome web browser as it works to address ...