djacidfx
Last seen: 1 month ago
Passionate small family-based developer creating innovative solutions with a personal touch. Simplifying complexities one line of code at a time.
Mirai Variant Murdoc Botnet Exploits AVT...
Cybersecurity researchers have warned of a new large-scale campaign that exploits security flaws in AVTECH IP cameras and Huawei H...
13,000 MikroTik Routers Hijacked by Botn...
A global network of about 13,000 hijacked Mikrotik routers has been employed as a botnet to propagate malware via spam campaigns, ...
Ex-CIA Analyst Pleads Guilty to Sharing ...
A former analyst working for the U.S. Central Intelligence Agency (CIA) pleaded guilty to transmitting top secret National Defense...
HackGATE: Setting New Standards for Visi...
Imagine receiving a penetration test report that leaves you with more questions than answers. Questions like, "Were all functional...
PNGPlug Loader Delivers ValleyRAT Malwar...
Cybersecurity researchers are calling attention to a series of cyber attacks that have targeted Chinese-speaking regions like Hong...
CERT-UA Warns of Cyber Scams Using Fake ...
The Computer Emergency Response Team of Ukraine (CERT-UA) is warning of ongoing attempts by unknown threat actors to impersonate t...
Unsecured Tunneling Protocols Expose 4.2...
New research has uncovered security vulnerabilities in multiple tunneling protocols that could allow attackers to perform a wide r...
DoNot Team Linked to New Tanzeem Android...
The Threat actor known as DoNot Team has been linked to a new Android malware as part of highly targeted cyber attacks. The artifa...
⚡ THN Weekly Recap: Top Cybersecurity Th...
As the digital world becomes more complicated, the lines between national security and cybersecurity are starting to fade. Recent ...
Product Walkthrough: How Satori Secures ...
Every week seems to bring news of another data breach, and it’s no surprise why: securing sensitive data has become harder than ev...
Patch Management Policy
Patching of operating systems, applications, and devices is not usually ranked as a favorite endeavor of IT professionals, but it’...
How to Spot a Phishing Email Attempt
Phishing attacks are one of the most common types of data breach attempts, with 3.4 billion phishing emails being sent every singl...
Penetration Testing and Scanning Policy
System or network vulnerabilities and security threats can severely impact business operations or even shutter its doors. However,...
Linux Kernel 6.13 Released with Big Chan...
The first new kernel release of the year has arrived — yes, Linux 6.13 has gone stable. Linux kernel 6.13 adds, as ever, a vast ar...
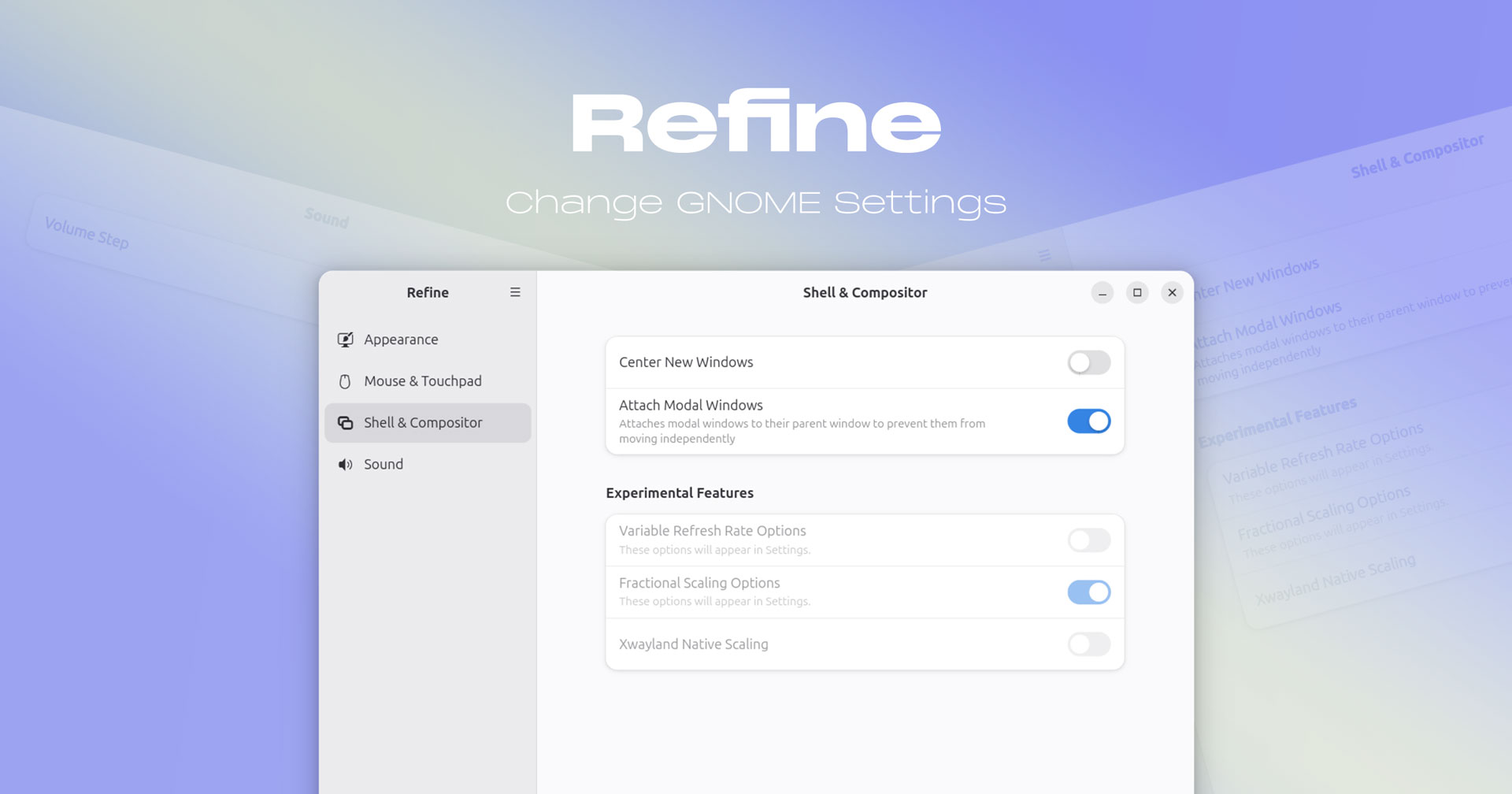
Refine (Advanced GNOME Settings Apps) Ad...
A clutch of new customisation and configuration options were added to Refine, a GTK4/libadwaita app in the vein of GNOME Tweaks (b...
Def Leppard Plays First 2025 Show Withou...
Guitarist sat out while continuing cancer treatment. Continue reading…
How Dickey Betts Helped Warren Haynes
The late Allman Brothers Band guitarist opened an important door. Continue reading…
10 Rock Stars' Favorite Alcoholic Drinks
Cheers to rock 'n' roll. Continue reading…
John Fogerty, Stevie Wonder, Black Crowe...
Graham Nash, Alanis Morissette and pop star Olivia Rodrigo are also among the latest additions to the benefit event. Continue rea...
John Sykes of Thin Lizzy and Whitesnake ...
Official statement confirms that he'd been battling cancer. Continue reading…









![⚡ THN Weekly Recap: Top Cybersecurity Threats, Tools and Tips [20 January]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEibUYtFkTwqS47YcUb7TUXjh3O_hy4EpcleWFJwMJbNsMDq7put9WHNzJ7DzL91ft_fkec3WiI4HLOimL-vxg5z3JBwvRQC69CxVTc3n11Gsi9a19wru6TduDUV921EdMQhbWtF7GySZemOaPRhygWbQxOEthbms_qodBav8RnhE7XRnhT8wmLaNB4XvRle/s1600/recap.png?#)