Category: Main
2,500+ Truesight.sys Driver Variants Exploited to ...
A large-scale malware campaign has been found leveraging a vulnerable Windows driver associated with Adlice's product suite to sid...
GitVenom Malware Steals $456K in Bitcoin Using Fak...
Cybersecurity researchers are calling attention to an ongoing campaign that's targeting gamers and cryptocurrency investors under ...
FatalRAT Phishing Attacks Target APAC Industries U...
Various industrial organizations in the Asia-Pacific (APAC) region have been targeted as part of phishing attacks designed to deli...
Two Actively Exploited Security Flaws in Adobe and...
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added two security flaws impacting Adobe ColdFusion and Oracl...
Hackers Exploited Krpano Framework Flaw to Inject ...
A cross-site scripting (XSS) vulnerability in a virtual tour framework has been weaponized by malicious actors to inject malicious...
Leaked Black Basta Ransomware Chat Logs Reveal Inn...
More than a year's worth of internal chat logs from a ransomware gang known as Black Basta have been published online in a leak th...
SOC 3.0 - The Evolution of the SOC and How AI is E...
Organizations today face relentless cyber attacks, with high-profile breaches hitting the headlines almost daily. Reflecting on a ...
New Linux Malware ‘Auto-Color’ Grants Hackers Full...
Universities and government organizations in North America and Asia have been targeted by a previously undocumented Linux malware ...
Three Password Cracking Techniques and How to Defe...
Passwords are rarely appreciated until a security breach occurs; suffice to say, the importance of a strong password becomes clear...
CERT-UA Warns of UAC-0173 Attacks Deploying DCRat ...
The Computer Emergency Response Team of Ukraine (CERT-UA) on Tuesday warned of renewed activity from an organized criminal group i...
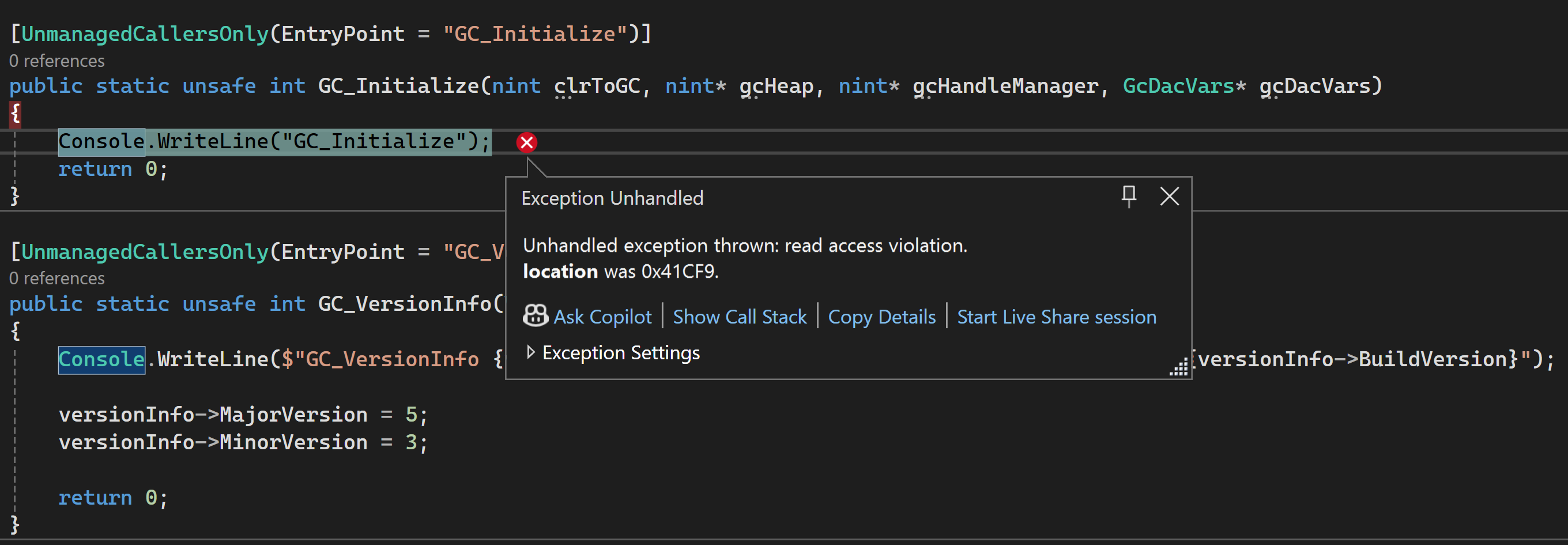
The JIT Calculator Challenge
Comments
I Went to SQL Injection Court
Comments