Category: Main
I Love Apple’s New OS Naming System—Hardware Shoul...
OS version numbers have been streamlined, but hardware names are messy.
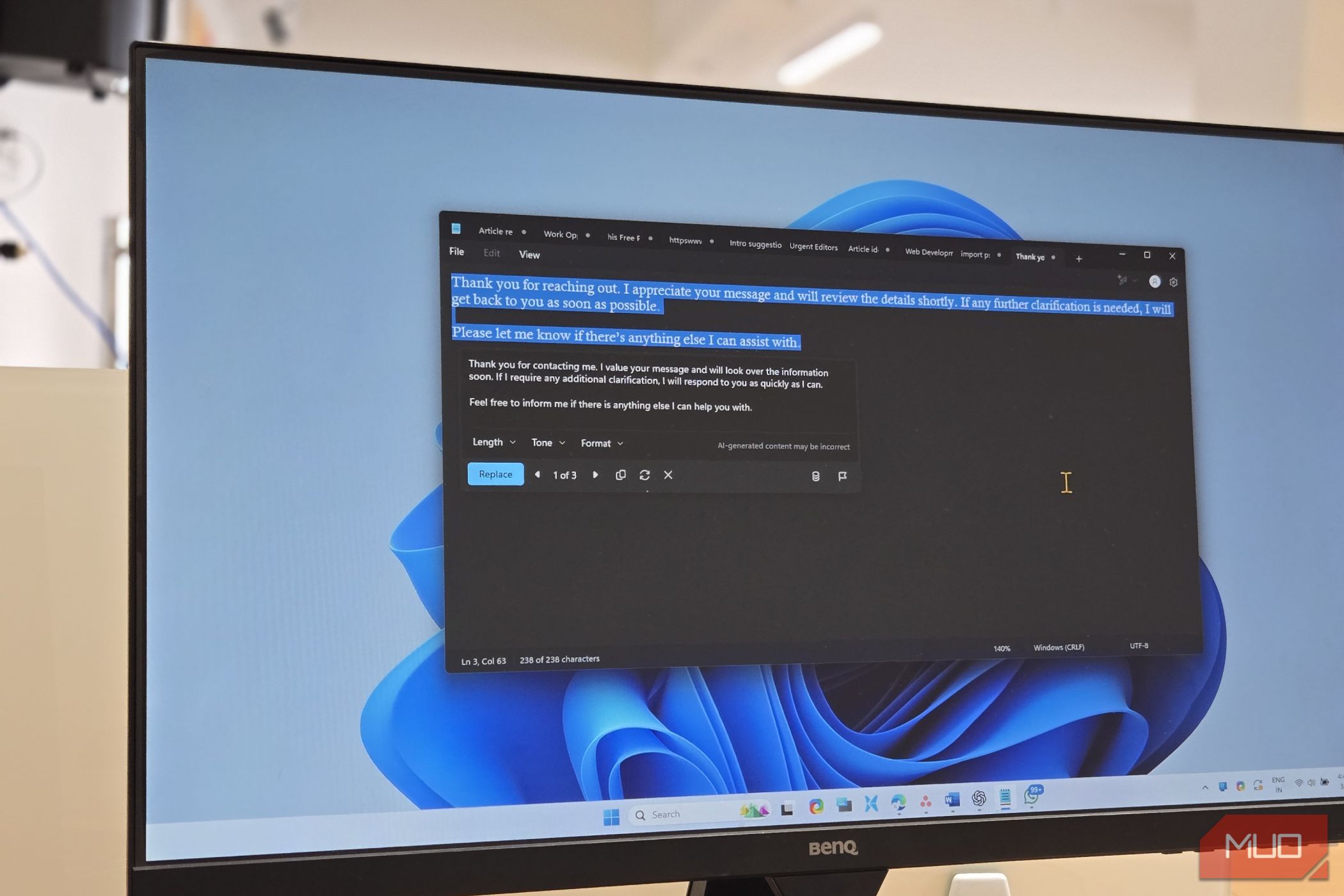
If You've Ignored Notepad Before, It’s Time to Tak...
Notepad is a more capable tool than we give it credit for.
I Don't Trust Chrome's Incognito Mode—I Use This B...
Chrome's Incognito mode isn't as private as you think.
AWOL Day Sale: Save Big on Home Theater Bundles Be...
This article is sponsored by AWOL Vision.
I'm Done With Chrome on Android: Here's What I Use...
It's the default, but I've found a better option.
6 Simple Ways to Get More Performance From Your NV...
These tweaks don't require expensive upgrades or technical headaches.
ONLYOFFICE Docs 9.0 Brings AI Smarts, Markdown Sup...
This post is sponsored by ONLYOFFICE.
New Android Malware Surge Hits Devices via Overlay...
Cybersecurity researchers have exposed the inner workings of an Android malware called AntiDot that has compromised over 3,775 dev...
BlueNoroff Deepfake Zoom Scam Hits Crypto Employee...
The North Korea-aligned threat actor known as BlueNoroff has been observed targeting an employee in the Web3 sector with deceptive...
Secure Vibe Coding: The Complete New Guide
DALL-E for coders? That’s the promise behind vibe coding, a term describing the use of natural language to create software. While ...
Uncover LOTS Attacks Hiding in Trusted Tools — Lea...
Most cyberattacks today don’t start with loud alarms or broken firewalls. They start quietly—inside tools and websites your busine...
Russian APT29 Exploits Gmail App Passwords to Bypa...
Threat actors with suspected ties to Russia have been observed taking advantage of a Google account feature called application spe...
Meta Adds Passkey Login Support to Facebook for An...
Meta Platforms on Wednesday announced that it's adding support for passkeys, the next-generation password standard, on Facebook. "...
New Linux Flaws Enable Full Root Access via PAM an...
Cybersecurity researchers have uncovered two local privilege escalation (LPE) flaws that could be exploited to gain root privilege...
New Malware Campaign Uses Cloudflare Tunnels to De...
A new campaign is making use of Cloudflare Tunnel subdomains to host malicious payloads and deliver them via malicious attachments...
1,500+ Minecraft Players Infected by Java Malware ...
A new multi-stage malware campaign is targeting Minecraft users with a Java-based malware that employs a distribution-as-service (...
FedRAMP at Startup Speed: Lessons Learned
For organizations eyeing the federal market, FedRAMP can feel like a gated fortress. With strict compliance requirements and a not...
Water Curse Employs 76 GitHub Accounts to Deliver ...
Cybersecurity researchers have exposed a previously unknown threat actor known as Water Curse that relies on weaponized GitHub rep...
Ex-CIA Analyst Sentenced to 37 Months for Leaking ...
A former U.S. Central Intelligence Agency (CIA) analyst has been sentenced to little more than three years in prison for unlawfull...
CISA Warns of Active Exploitation of Linux Kernel ...
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday placed a security flaw impacting the Linux kernel in i...